Ransomware Protection Built
for Predictable Recovery
Detect early. Verify deeply. Recover clean - across clouds in minutes.
Datamotive Easy Protect is a recovery-first ransomware protection capability that combines real-time behavioural detection with isolated, DR-side forensic validation into a single operational workflow.
Why Traditional Ransomware Protection Falls Short
Most ransomware solutions focus heavily on detection, while recovery remains slow,
complex,
and uncertain - especially in hybrid and multi-cloud environments.
-
Agent-based tools increase operational overhead and impact production performance.
-
Detection without validated recovery paths extends downtime.
-
Production-side scanning introduces risk during active incidents.
-
Recovery remains inconsistent across platforms, workloads, and clouds.
Ransomware is no longer just a security issue. It is a continuity challenge.
Recovery-First Ransomware Protection
Easy Protect is designed around recovery readiness - not just alerting.
Core Characteristics
-
Agentless, non-intrusive protection at block and hypervisor level without impacting production workloads.
-
Recovery-first ransomware protection with validated paths in advance and reduced reinfection risk.
-
Inline, real-time anomaly detection with sub-100ms behavioural analysis without slowing replication.
-
Automated and policy-driven validation through DR-side scans with admin-controlled responses.
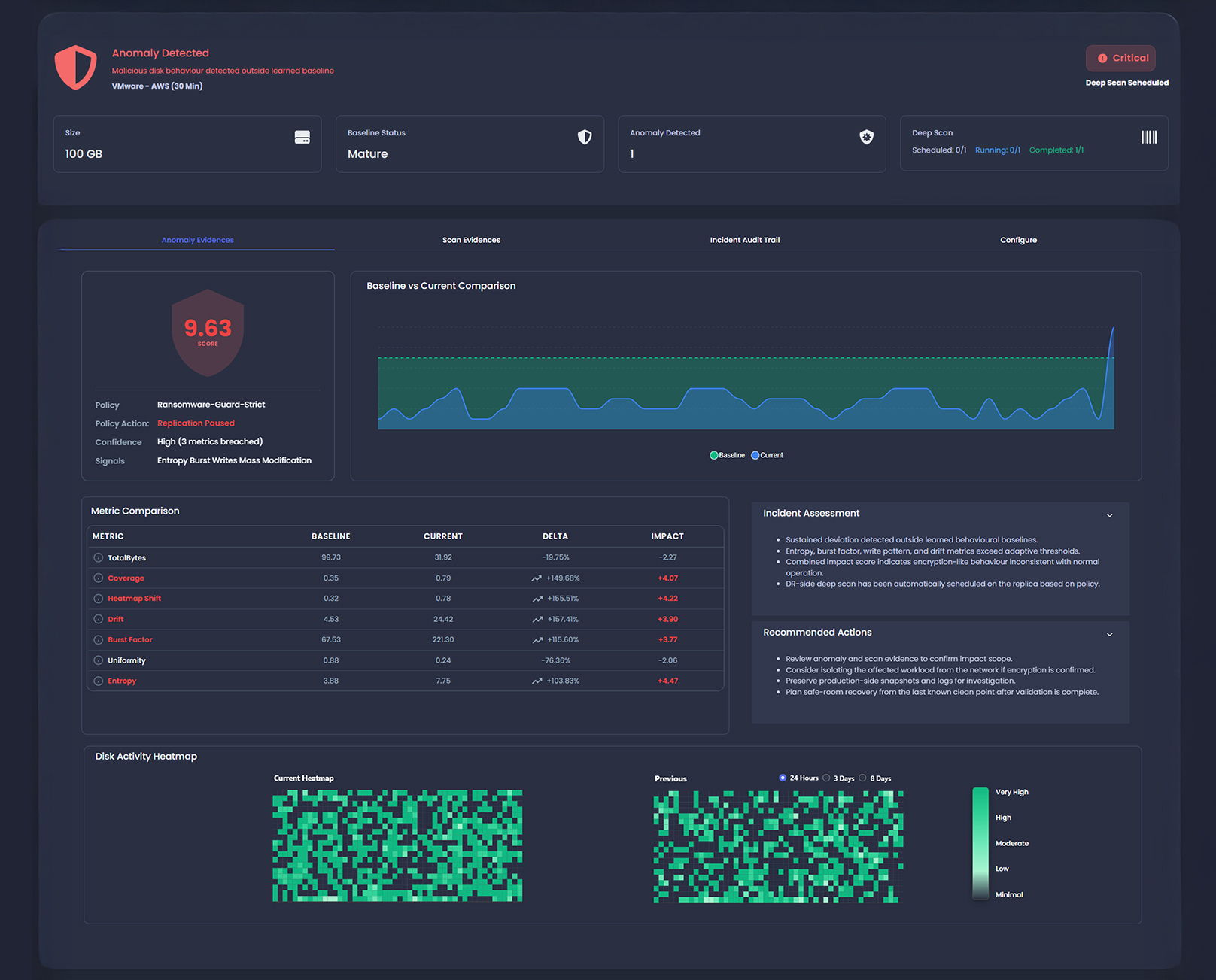
Inline, Behavioural Anomaly Detection
Block-level, real-time behavioral analysis with continuously learning multi-timescale (n-baseline) models and adaptive thresholds, enabling policy-based control to pause or continue replication.
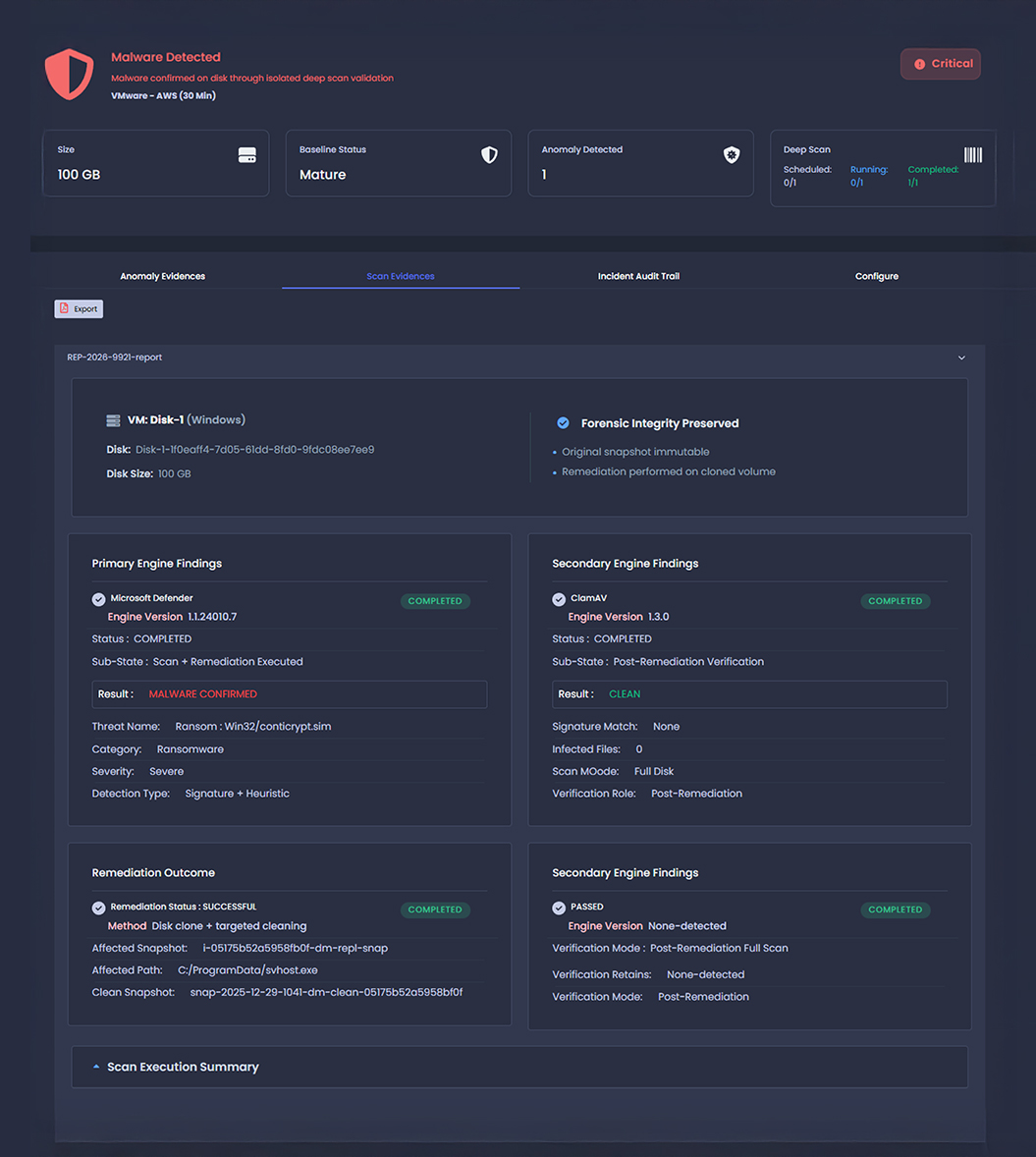
Remote, Offline Deep Scanning
Recovery replicas are validated in isolation using a pluggable deep-scan framework that integrates with third-party security engines such as Microsoft Defender, ClamAV, and other 3rd party engines
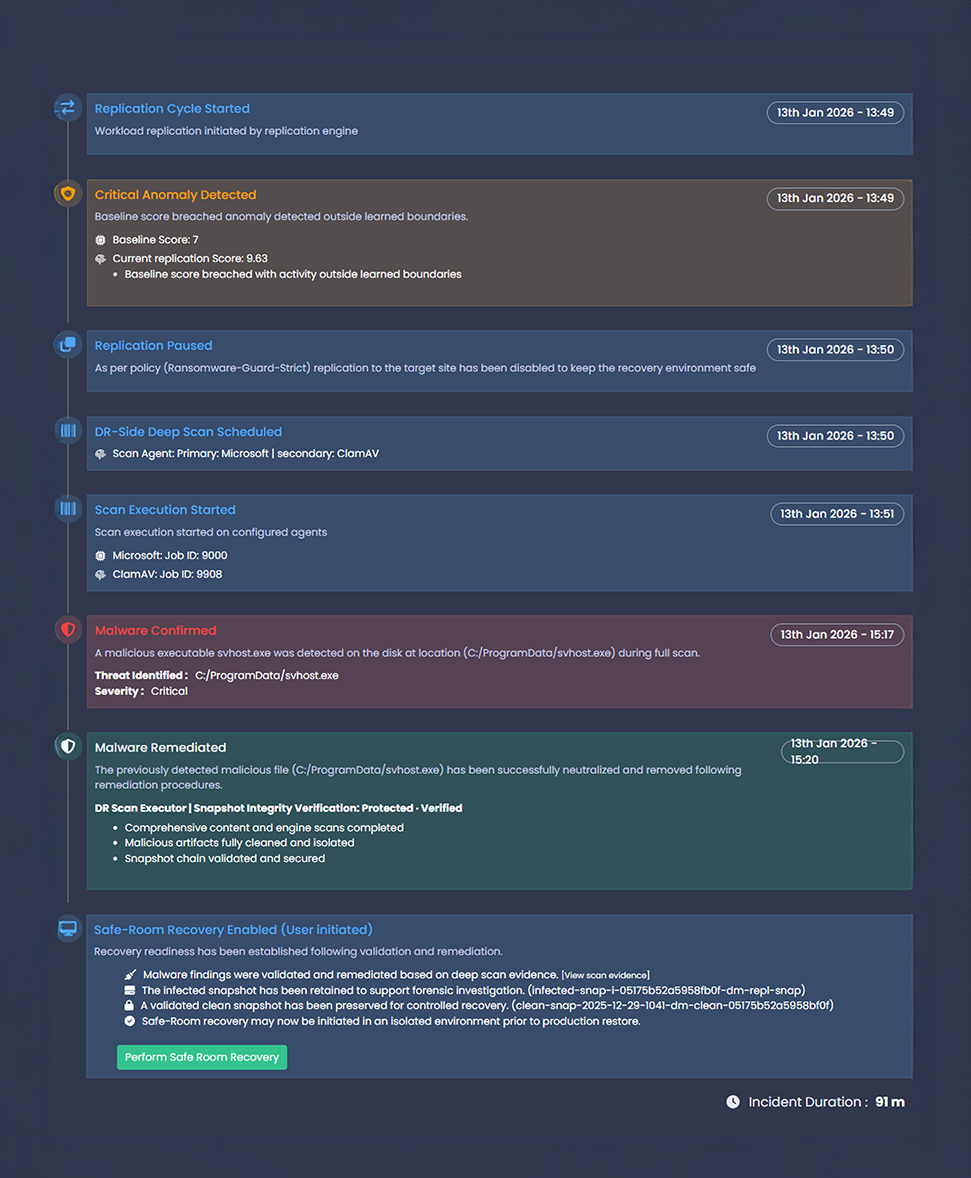
Automated Detection, Validation, and Response
- Anomalous behavior detected during replication initiates policy-driven validation workflows without disrupting production.
- DR-side deep scans are automatically scheduled to assess recovery data in an isolated environment.
- Remediation actions are applied to affected replicas while preserving clean recovery points.
- Safe-Room recovery is enabled from a validated state, with a complete, auditable incident trail.
Detection Alone Does Not Define Resilience
Early detection is important. Clean, predictable recovery is what defines resilience.
With Easy Protect
- Recovery readiness is continuously verified, not assumed.
- Clean recovery points are identified in advance, reducing decision time during an incident.
- Recovery outcomes remain predictable across clouds, applications, and workload sizes.
- Downtime, disruption, and reinfection risk are minimized through validated replicas.
- Business operations recover faster with less manual effort and fewer escalations.
Resilience is proven by recovery — not just detection.